Insider Betrayals: The Trust Breach That Tech Cannot Detect
Cybersecurity doctrine has long emphasized perimeter defenses and technical intrusion detection. Yet, one of the most devastating attack vectors bypasses both entirely: the insider. Whether motivated by ideology, personal grievance, coercion, or financial gain, insider threats cut through layers of technical control by virtue of legitimate access.
The Anatomy of a Modern Insider Threat
Gone are the days of the disgruntled employee with a USB stick. Today’s insider betrayer may be a contractor embedded via third-party firms, a software engineer siphoning intellectual property through obfuscated commits, or a DevOps administrator quietly exfiltrating credentials to darknet buyers.
Notable examples include:
- Edward Snowden’s data exfiltration at NSA, which redefined public understanding of surveillance and insider risk.
- Tesla’s internal sabotage in 2018, involving intentional code alteration and data theft.
- 2022’s Conti Leaks, where a Trickbot affiliate leaked over 60,000 messages exposing the group’s ransomware operations from within.
The asymmetry is stark: organizations often invest heavily in defending against external actors but remain ill-equipped to detect betrayal by those inside the firewall.
Mitigation Requires Cultural and Technical Synthesis
Behavioral analytics, context-aware monitoring, and zero-trust architectures can detect anomalous behavior—but only when culturally supported. Too often, security tools are siloed from HR, legal, and managerial oversight. Insider threat programs must fuse cyber telemetry with human insight—monitoring not only the ‘what’ but also the ‘why.’
State-Backed Exploits: The Quiet Wars Behind Firewalls
While nation-states have long engaged in espionage, the scale, sophistication, and deniability of state-sponsored cyber campaigns have transformed digital conflict into a continuous low-intensity war. The line between cybercrime and geopolitical sabotage is now indistinguishably blurred.
Strategic Exploitation of Supply Chains
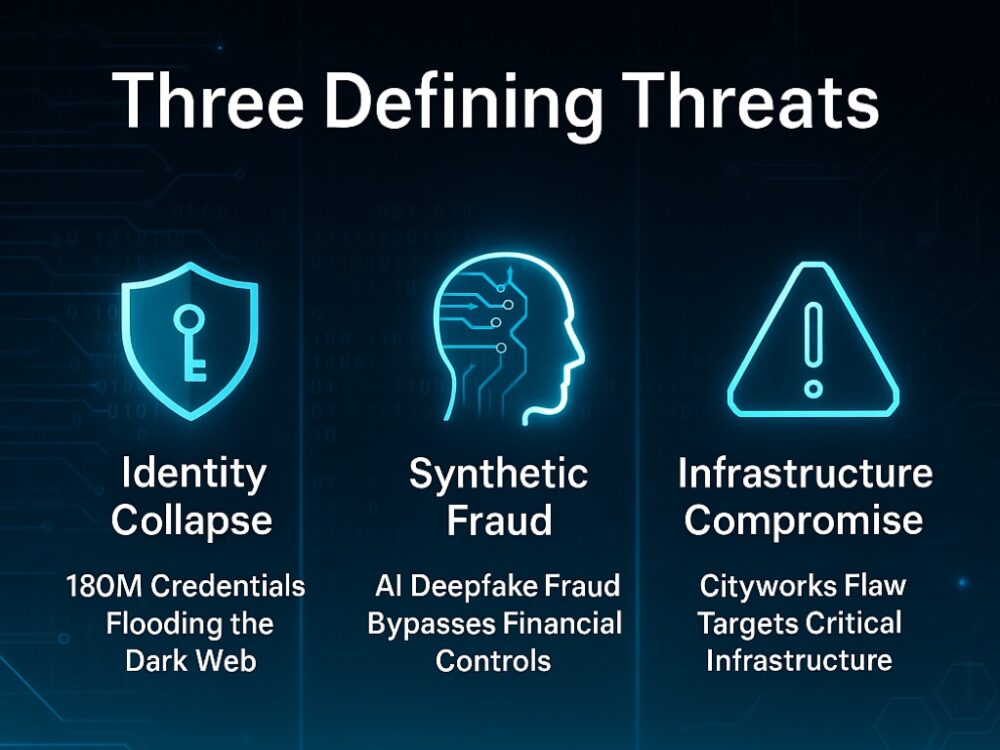
Operations like SolarWinds (2020), Microsoft Exchange Server exploits (2021), and the Cityworks vulnerability exploited in 2025 demonstrate the systemic nature of modern state threats. By embedding malware into widely used software systems, adversaries gain leverage not over single organizations—but entire national infrastructures.
Recent threat actor trends:
- APT29 (Russia) targeting identity systems and federated trust chains via “Magic Web” malware.
- APT41 (China) exploiting CI/CD pipelines, code signing services, and adversary-in-the-middle attacks to hijack software update mechanisms.
- North Korea’s Lazarus Group monetizing exploits through ransomware and crypto theft, merging espionage with financial coercion.
The Nation-State as a Crime Syndicate
Some actors blend espionage with profit-seeking. State-affiliated groups moonlight as ransomware operators, funneling stolen data to state intelligence while demanding payment from victims. This creates legal ambiguity: are they criminals, combatants, or both?
Defense Requires Political Will and Public-Private Partnership
Traditional cyber defense models—patching, firewalls, AV—are insufficient. Governments must prioritize attribution, impose costs, and support sectoral cyber hardening. Meanwhile, enterprises must shift from compliance-based security to resilience-first models, embedding threat intelligence into procurement, vendor management, and code audits.
AI’s Fragile Defenses: Accelerating Innovation, Neglecting Security
As enterprises rapidly deploy artificial intelligence across workflows, a dangerous assumption persists: that AI systems are inherently safe. In reality, AI’s attack surface is expanding faster than the defenses around it.
The Myth of Secure Intelligence
AI systems are highly vulnerable—not because they are inherently flawed, but because:
- They lack contextual awareness. AI agents can be manipulated through prompt injection, instructional corruption, or indirect input poisoning.
- They operate on opaque logic. Deep learning models exhibit brittle behavior under slight perturbations, enabling adversarial attacks.
- They interact autonomously. Connected AI agents now have write-access to systems, can initiate transactions, or modify infrastructure—all while lacking the ability to verify intent.
Recent cases:
- DeepSeek R1, a foundational LLM, was breached via prompt injection with a 100% success rate.
- Langflow, a popular AI orchestration platform, was added to CISA’s Known Exploited Vulnerabilities list after adversaries used it to escalate privileges in enterprise environments.
- Synthetic identity fraud, where AI-generated voice clones of CFOs authorized wire transfers—showing that AI-generated deception can now bypass social and procedural controls.
Defending the Machine Brain
To secure AI, organizations must:
- Red-team AI systems with adversarial simulation before deployment.
- Isolate AI agents in sandboxed environments and limit their privileges.
- Implement deterministic guardrails, not just probabilistic filters.
- Treat AI not as an augmentation layer—but as a dynamic risk surface that requires full-spectrum oversight.
Convergence and Implications: The Triangulation of Crisis
Each of these threats—insider betrayal, state-backed intrusion, and AI insecurity—poses catastrophic risk on its own. But in practice, they are converging:
- A state actor might recruit insiders or bribe contractors.
- Insiders may exploit vulnerabilities in AI systems to cover their actions.
- AI agents could be subverted to amplify the damage from state-level exploits or insider sabotage.
The result is a multi-vector threat landscape, where detection is late, attribution is obscured, and mitigation is increasingly reactive.
Toward a Post-Perimeter Security Ethic
Addressing this triptych of instability requires abandoning outdated assumptions:
- Trust must be continuously earned, not statically granted.
- AI must be treated as both a tool and a liability.
- Security must be embedded at every operational layer—not bolted on post-deployment.
This means deploying zero-trust identity architectures, expanding telemetry analysis across human and synthetic actors, and recognizing that the most dangerous breaches may originate not from the outside, but from those who already hold the keys.
Final Reflection
The age of isolated cyber threats is over. We have entered an era of entangled risk, where betrayal may originate internally, be sponsored externally, and be executed by artificial agents. The defenders of today must learn to operate in ambiguity, build for disruption, and assume nothing.
Cybersecurity is no longer a technical domain—it is a geopolitical, psychological, and algorithmic battlefield. And the front lines run through every employee, every AI process, and every vendor API.
To survive the next decade, we must adapt to this reality—not as a challenge, but as the new normal.










 Puru's [AI]
Puru's [AI]
