Reports consistently highlight persistent threats emanating from countries like China and North Korea, whose cyber units leverage these vulnerabilities for espionage, intellectual property theft, and strategic disruption.
Posts/Articles
Victim of a Cybercrime? Looking for Sophisticated Cyber-Forensic Support?
The world is digitally connected; the digital landscape is vast; while offering unparalleled convenience and innovation as digital incentives, undoubtedly it also harbors a growing number of threats. Cybercrime has evolved from niche attacks to a pervasive and sophisticated industry, impacting individuals, businesses, and even governments on an unprecedented scale. If you’ve found yourself asking, “Am I a victim of a cybercrime?”, understanding the signs and knowing where to turn for help is paramount.
The Alarming Rise of Cybercrime
Cybercrime encompasses a vast array of illicit activities conducted through computer networks or the internet. From financial fraud and identity theft to massive data breaches and ransomware attacks, the motives are diverse, ranging from monetary gain to espionage or disruption. Recent statistics paint a stark picture: global cybercrime costs are projected to reach trillions of dollars annually in the coming years, with attacks becoming more frequent and complex.Malware, phishing, ransomware, and social engineering continue to be primary vectors, often preying on human vulnerabilities as much as technological ones.
How to Recognize if You’ve Been Targeted
Being a victim of cybercrime isn’t always obvious. While some attacks, like ransomware locking your files, are undeniable, others can be insidious and go unnoticed for months. Here are common indicators that you might be a victim:
- Unusual Activity on Your Accounts: Unauthorized transactions on bank statements or credit cards, suspicious login alerts from unrecognized devices or locations, or changes to passwords you didn’t initiate.
- Phishing Attempts and Suspicious Messages: Receiving emails or texts that appear to be from legitimate sources but contain urgent requests, suspicious links, or unfamiliar sender addresses. Friends or colleagues reporting strange messages sent from your email or social media accounts.
- Device Performance Issues: Your computer or smartphone suddenly running very slowly, frequent crashes, unexpected pop-up ads, or new, unfamiliar software appearing on your device.
- Locked or Encrypted Files: Finding your files inaccessible, often accompanied by a demand for payment to restore access (ransomware).
- Identity Theft Indicators: Receiving bills or debt collection notices for accounts you didn’t open, or alerts about tax filings in your name that you didn’t authorize.
- Data Breach Notifications: Being informed by a company that your personal information was exposed in a data breach.
The Indispensable Role of Cyber-Forensic Support
Once you suspect a cybercrime, swift and decisive action is critical. This is where cyber-forensic support becomes indispensable. Cyber forensics, often referred to as digital forensics, is the science of uncovering, analyzing, and preserving digital evidence from computers, networks, and other digital devices to investigate cyber incidents. It’s the investigative arm of cybersecurity, crucial for understanding what happened, how it happened, and who was responsible.
Cyber-forensic professionals are the digital detectives who can piece together the story of a cyberattack. Their expertise goes beyond simply identifying the breach; they work to:
- Preserve Evidence: Crucially, they ensure that digital evidence is collected and preserved in a forensically sound manner, maintaining its integrity so it can be admissible in legal proceedings, if necessary.
- Identify the Breach’s Scope and Origin: They meticulously analyze network traffic, system logs, and compromised devices to pinpoint the entry points, the extent of data exfiltration, and the techniques used by the attackers.
- Recover Lost or Corrupted Data: In many cases, they can recover encrypted, damaged, or deleted files, helping victims restore their operations.
- Determine Impact and Vulnerabilities: They assess the full impact of the attack, identify system weaknesses, and provide recommendations to strengthen defenses against future incidents.
- Support Legal Action: Their detailed reports and expert testimony can be vital in prosecuting cybercriminals, recovering losses, or complying with regulatory requirements.
Why Professional Expertise Matters
Attempting to investigate a cybercrime on your own can lead to further data loss, contamination of evidence, or even unknowingly providing more access to the attacker. Cyber-forensic specialists possess the unique blend of technical knowledge, legal understanding, and specialized tools required to navigate complex digital environments. They understand the intricacies of various operating systems, network protocols, and attack methodologies, enabling them to reconstruct events and provide actionable insights.
The threat of cybercrime is ever-present and continually evolving. Being a victim can be a deeply unsettling and damaging experience, impacting your finances, privacy, and peace of mind. However, you don’t have to face it alone. If you are a victim of such cybercrime and are looking for sophisticated cyber-forensic support, find professionals at puru.link to have an in-person or remote consultation. Engaging with experienced cyber-forensic experts is the most effective way to understand the nature of the attack, mitigate its damage, and secure your digital future.
Entangled Insider Betrayals, Nation-State Exploits, and the Insecurity of Intelligent Systems
Insider Betrayals: The Trust Breach That Tech Cannot Detect
Cybersecurity doctrine has long emphasized perimeter defenses and technical intrusion detection. Yet, one of the most devastating attack vectors bypasses both entirely: the insider. Whether motivated by ideology, personal grievance, coercion, or financial gain, insider threats cut through layers of technical control by virtue of legitimate access.
The Anatomy of a Modern Insider Threat
Gone are the days of the disgruntled employee with a USB stick. Today’s insider betrayer may be a contractor embedded via third-party firms, a software engineer siphoning intellectual property through obfuscated commits, or a DevOps administrator quietly exfiltrating credentials to darknet buyers.
Notable examples include:
- Edward Snowden’s data exfiltration at NSA, which redefined public understanding of surveillance and insider risk.
- Tesla’s internal sabotage in 2018, involving intentional code alteration and data theft.
- 2022’s Conti Leaks, where a Trickbot affiliate leaked over 60,000 messages exposing the group’s ransomware operations from within.
The asymmetry is stark: organizations often invest heavily in defending against external actors but remain ill-equipped to detect betrayal by those inside the firewall.
Mitigation Requires Cultural and Technical Synthesis
Behavioral analytics, context-aware monitoring, and zero-trust architectures can detect anomalous behavior—but only when culturally supported. Too often, security tools are siloed from HR, legal, and managerial oversight. Insider threat programs must fuse cyber telemetry with human insight—monitoring not only the ‘what’ but also the ‘why.’
State-Backed Exploits: The Quiet Wars Behind Firewalls
While nation-states have long engaged in espionage, the scale, sophistication, and deniability of state-sponsored cyber campaigns have transformed digital conflict into a continuous low-intensity war. The line between cybercrime and geopolitical sabotage is now indistinguishably blurred.
Strategic Exploitation of Supply Chains
Operations like SolarWinds (2020), Microsoft Exchange Server exploits (2021), and the Cityworks vulnerability exploited in 2025 demonstrate the systemic nature of modern state threats. By embedding malware into widely used software systems, adversaries gain leverage not over single organizations—but entire national infrastructures.
Recent threat actor trends:
- APT29 (Russia) targeting identity systems and federated trust chains via “Magic Web” malware.
- APT41 (China) exploiting CI/CD pipelines, code signing services, and adversary-in-the-middle attacks to hijack software update mechanisms.
- North Korea’s Lazarus Group monetizing exploits through ransomware and crypto theft, merging espionage with financial coercion.
The Nation-State as a Crime Syndicate
Some actors blend espionage with profit-seeking. State-affiliated groups moonlight as ransomware operators, funneling stolen data to state intelligence while demanding payment from victims. This creates legal ambiguity: are they criminals, combatants, or both?
Defense Requires Political Will and Public-Private Partnership
Traditional cyber defense models—patching, firewalls, AV—are insufficient. Governments must prioritize attribution, impose costs, and support sectoral cyber hardening. Meanwhile, enterprises must shift from compliance-based security to resilience-first models, embedding threat intelligence into procurement, vendor management, and code audits.
AI’s Fragile Defenses: Accelerating Innovation, Neglecting Security
As enterprises rapidly deploy artificial intelligence across workflows, a dangerous assumption persists: that AI systems are inherently safe. In reality, AI’s attack surface is expanding faster than the defenses around it.
The Myth of Secure Intelligence
AI systems are highly vulnerable—not because they are inherently flawed, but because:
- They lack contextual awareness. AI agents can be manipulated through prompt injection, instructional corruption, or indirect input poisoning.
- They operate on opaque logic. Deep learning models exhibit brittle behavior under slight perturbations, enabling adversarial attacks.
- They interact autonomously. Connected AI agents now have write-access to systems, can initiate transactions, or modify infrastructure—all while lacking the ability to verify intent.
Recent cases:
- DeepSeek R1, a foundational LLM, was breached via prompt injection with a 100% success rate.
- Langflow, a popular AI orchestration platform, was added to CISA’s Known Exploited Vulnerabilities list after adversaries used it to escalate privileges in enterprise environments.
- Synthetic identity fraud, where AI-generated voice clones of CFOs authorized wire transfers—showing that AI-generated deception can now bypass social and procedural controls.
Defending the Machine Brain
To secure AI, organizations must:
- Red-team AI systems with adversarial simulation before deployment.
- Isolate AI agents in sandboxed environments and limit their privileges.
- Implement deterministic guardrails, not just probabilistic filters.
- Treat AI not as an augmentation layer—but as a dynamic risk surface that requires full-spectrum oversight.
Convergence and Implications: The Triangulation of Crisis
Each of these threats—insider betrayal, state-backed intrusion, and AI insecurity—poses catastrophic risk on its own. But in practice, they are converging:
- A state actor might recruit insiders or bribe contractors.
- Insiders may exploit vulnerabilities in AI systems to cover their actions.
- AI agents could be subverted to amplify the damage from state-level exploits or insider sabotage.
The result is a multi-vector threat landscape, where detection is late, attribution is obscured, and mitigation is increasingly reactive.
Toward a Post-Perimeter Security Ethic
Addressing this triptych of instability requires abandoning outdated assumptions:
- Trust must be continuously earned, not statically granted.
- AI must be treated as both a tool and a liability.
- Security must be embedded at every operational layer—not bolted on post-deployment.
This means deploying zero-trust identity architectures, expanding telemetry analysis across human and synthetic actors, and recognizing that the most dangerous breaches may originate not from the outside, but from those who already hold the keys.
Final Reflection
The age of isolated cyber threats is over. We have entered an era of entangled risk, where betrayal may originate internally, be sponsored externally, and be executed by artificial agents. The defenders of today must learn to operate in ambiguity, build for disruption, and assume nothing.
Cybersecurity is no longer a technical domain—it is a geopolitical, psychological, and algorithmic battlefield. And the front lines run through every employee, every AI process, and every vendor API.
To survive the next decade, we must adapt to this reality—not as a challenge, but as the new normal.
Legacy of a Cybercrime Empire: Trickbot and the Industrialization of Ransomware
The cybercriminal ecosystem of 2025 still bears the fingerprints of one of the most formidable threat actors of the last decade: Trickbot. Though officially dismantled, Trickbot’s methodologies, tools, and organizational model have become foundational to modern ransomware operations. More than a gang, it was an institution—an archetype of what professionalized cybercrime looks like. And its shadow still shapes today’s threat landscape.
The Emergence of a Cyber Syndicate
Trickbot began as a banking trojan in 2016, designed to siphon credentials from financial institutions. But over six years, it evolved into a criminal empire, culminating in the development of its own ransomware arm—Conti. At its peak, Trickbot wasn’t just delivering malware; it was orchestrating industrial-scale campaigns with militarized precision.
This wasn’t a loose hacker collective—it was a fully operational business. Internal leaks from 2022 revealed an organization with HR departments, QA teams, payroll managers, and scheduled vacation requests. Leaders like Maksim Rudenskiy, Maksim Galochkin, and Mikhail Tsarev ran development, testing, and finance, mirroring the structure of a modern tech startup.
“You cannot convince me they weren’t running this exactly like a tech startup,” said Jake Williams, former NSA operator.
Technical Innovation Through Modularity
Trickbot’s defining technical breakthrough was modularity. It developed a malware ecosystem where attacks could be custom-built using Lego-like components. The core loader enabled persistence and beaconing. Payloads were tailored: credential stealers, web injectors, lateral movement tools, and remote access modules—all deployed dynamically based on victim profiles.
This modularity allowed for:
- Fast iteration without re-compiling core binaries.
- Reduced detection footprints through isolated functionality.
- Controlled testing of new capabilities on segmented targets.
“Trickbot built a menu where every attack could be customized. They industrialized cybercrime.” —Sarah Chen, malware analyst
Infrastructure as a Weapon
At its operational zenith, Trickbot maintained 128+ command servers globally. These weren’t just redundant—they were strategically distributed across countries like Brazil, Kyrgyzstan, and Colombia to complicate takedown efforts. Communications were encrypted and often layered with fallback domain generation algorithms.
They also pioneered parasitic infrastructure—co-opting infected victim machines as proxy nodes, effectively turning victims into parts of the attack infrastructure.
Procurement and ops security were equally disciplined. Servers were bought using false identities, cryptocurrencies, and bulletproof hosting arrangements. Failover systems activated within hours of takedowns.
Strategic Alliances and Ransomware-as-a-Service
Trickbot’s most disruptive move wasn’t a tool—but a partnership: its alliance with Emotet, which enabled mass deployment via email spam. Emotet infections became Trickbot entry points. In return, Trickbot paid per successful install.
This ecosystem strategy extended to:
- Ryuk and Conti ransomware operations
- QakBot and IcedID malware exchanges
- Initial Access Brokers and Money Laundering Networks
This cooperative model scaled attacks beyond any single actor’s capacity, laying the groundwork for today’s Ransomware-as-a-Service (RaaS) model.
Tactical Maturity in Ransomware Deployment
By 2020, Trickbot had fully transitioned from fraud to ransomware. It wasn’t smash-and-grab; it was surveillance and siege. Operators infiltrated systems for weeks before deploying encryption. They harvested sensitive data to fuel double extortion schemes, maximizing pressure on victims.
During the COVID-19 pandemic, Trickbot targeted healthcare networks—explicitly because “they pay fastest.” Over 400 healthcare organizations were hit in 2020 alone. The targeting was calculated, heartless, and efficient.
Affiliates handled execution. Trickbot provided tools and infrastructure, taking a cut—70/30 or 80/20 depending on performance.
Operational Immunity and Law Enforcement Hurdles
Operating from Russia provided near-complete immunity. Extradition was impossible. Arrests only occurred when members traveled abroad. The infrastructure was globally distributed; the operators remained untouched.
Even large-scale operations—like Microsoft’s 2020 takedown of over 100 servers—only momentarily disrupted operations. Encrypted C2, fast-changing payloads, and affiliate-based distribution ensured continuity.
The real breach came from within: The Conti Leaks. In 2022, an insider released over 60,000 internal messages, unmasking operators and exposing operational blueprints. It sowed distrust, fractured alliances, and crippled internal morale.
Trickbot’s Demise and Fragmentation
Under increasing pressure, Trickbot formally disbanded in 2022. But its dissolution created not peace, but proliferation. Its members splintered and seeded new operations: Black Basta, Royal, Quantum, Karakurt. Others joined LockBit, Hive, and similar groups.
They carried with them:
- Modular architecture designs
- Professionalized management structures
- Proven RaaS business models
- A ruthless understanding of operational targeting
Trickbot’s DNA became the ransomware standard.
Lessons for Modern Cyber Defense
The legacy of Trickbot offers a strategic playbook for defense in 2025 and beyond:
- Assume Professional Adversaries
These are not hobbyists. Defenders must account for adversaries with structured teams, operational discipline, and multi-stage tactics. - Focus on Behavior, Not Signatures
Modular malware evades static detection. Detect anomalous behavior: lateral movement, privilege escalation, unusual admin tools. - Prepare for Ecosystem Attacks
Modern intrusions involve multiple entities. Monitor for coordinated signals across the attack chain—not just individual indicators. - Build for Resilience, Not Just Prevention
Assume breach. Minimize dwell time. Prioritize rapid isolation and recovery. - Invest in Intelligence Sharing
Collaborating with threat intelligence groups and law enforcement multiplies defense effectiveness. The Conti Leaks proved that insider exposure can be more powerful than external takedowns.
The Aftermath and Ongoing Influence
Vitaly Nikolaevich Kovalev, Trickbot’s alleged leader—known online as Stern—remains at large in Russia. But the real story isn’t one of individual fugitives. It’s the systemic transformation Trickbot triggered.
Today, every modular malware, every affiliate-run ransomware campaign, and every infrastructure-resilient criminal syndicate owes something to Trickbot’s playbook. Their fall was real. But their framework lives on.
Trickbot’s rise teaches how cybercrime scaled.
Trickbot’s fall teaches how even sophisticated operations can collapse.
Trickbot’s legacy teaches what defenders must expect next.
In an era defined by digital risk, Trickbot was both blueprint and warning. What emerges next may wear a different name—but the tactics, the tools, and the ambition will feel very familiar. We’ve seen the prototype. The evolution is already here.
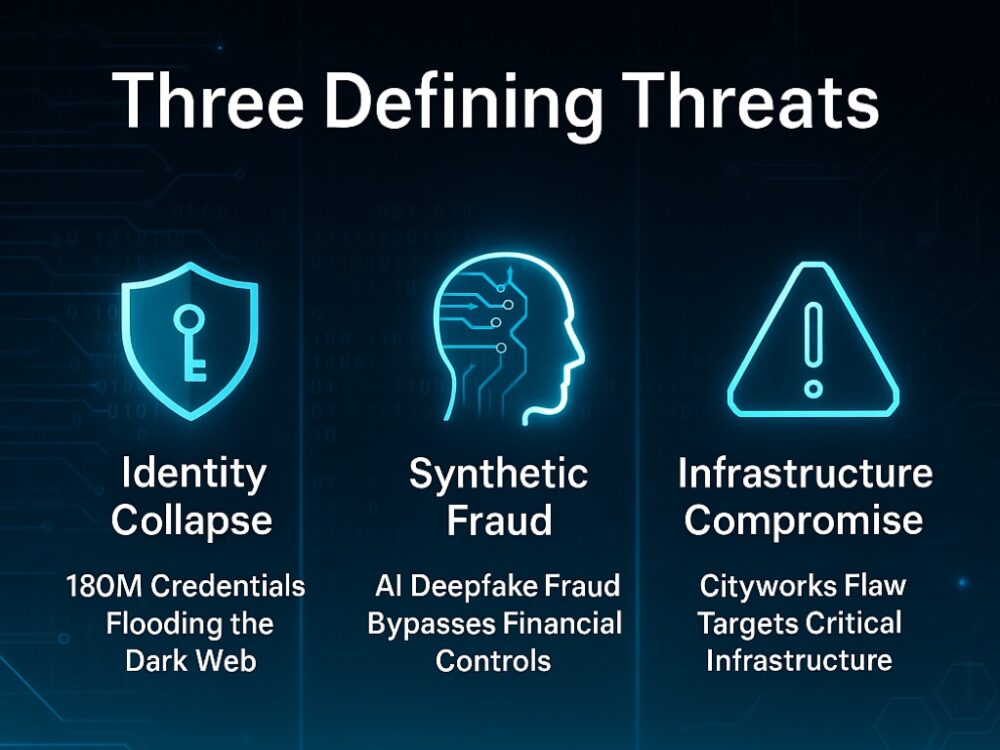
Identity Collapse, Synthetic Fraud, and Infrastructure Compromise
Enterprise security is facing a triad of compounding threats that are reshaping digital risk at scale. These are not isolated incidents; they are inflection points—each representing a category of systemic failure, accelerated by industrial-grade threat tooling and adversarial innovation. Below are three defining threats that demand immediate action.
Credential Flood: The Collapse of Password-Based Trust
A data leak exposing 180 million credentials—with roughly 30% still active—has flooded the dark web, fueling a renewed surge in credential stuffing attacks. These findings, consistent with IBM X-Force’s reporting on identity theft campaigns, confirm what security leaders have long feared: passwords have become liabilities.
This is no longer just a problem of end-user hygiene. The industrialization of credential harvesting—via infostealers, browser implants, and database breaches—has overwhelmed perimeter defenses. Legacy systems relying on password-based access are now actively complicit in breach propagation.
Implications:
- Password reuse is systemic, and real-time reuse detection is rare.
- Attackers exploit latency between breach and remediation.
- Active Directory deployments remain littered with weak credentials.
Required Actions:
- Expedite adoption of passwordless standards (e.g., FIDO2, WebAuthn).
- Audit identity stores—especially Active Directory—for vulnerable patterns.
- Deploy live credential monitoring against known dark web breaches.
Synthetic Fraud: Deepfakes as a Financial Weapon
A successful $2 million wire fraud executed using an AI-generated voice clone of a CFO has shattered assumptions about identity verification. The attack bypassed all technical controls—not by exploiting software, but by exploiting human trust in real-time communication.
This evolution in attack surface—where executive voices can be faked with precision and urgency is manufactured as a weapon—has redefined the nature of fraud. It is no longer enough to secure endpoints or encrypt traffic. The adversary is speaking directly into our workflows.
Implications:
- Verbal confirmation is no longer a verification layer—it is a vulnerability.
- Finance, HR, and legal departments are now frontline targets.
- Deepfake generation is accessible, scalable, and context-aware.
Required Actions:
- Mandate verbal MFA—callback authentication, biometric voiceprint checks, or internal codeword protocols—for high-risk approvals.
- Train staff to question urgency, even when the voice sounds “real.”
- Incorporate deepfake simulations into executive-level tabletop exercises.
Infrastructure Attack: Exploiting the Municipal Edge
Chinese state-aligned actors (UAT-6382) exploited a deserialization vulnerability (CVE-2025-0944) in Trimble Cityworks, breaching local government networks through compromised IIS web servers. Though patched in early 2025, this attack demonstrates the latency of municipal cyber hygiene and the rising fragility of niche operational technology (OT) platforms.
Critical infrastructure is now a favored terrain for nation-state actors—not because of the value of the software itself, but because of the value of disruption. Local government systems, poorly segmented and slow to patch, are increasingly leveraged for espionage, disruption, and broader lateral movement.
Implications:
- Vulnerabilities in obscure systems can yield strategic access.
- Public infrastructure remains underfunded and under-monitored.
- The OT/IT boundary is porous, especially in municipal deployments.
Required Actions:
- Patch Cityworks installations to v15.8.9 or later immediately.
- Deploy OT anomaly detection capable of identifying lateral movement.
- Conduct software provenance audits across the third-party stack.
A Converging Threat Landscape
The convergence of leaked credentials, synthetic identity fraud, and infrastructure compromise marks a transformation in the threat landscape. Each represents a collapse of a foundational trust assumption—passwords, voices, and critical systems. The adversaries are not merely evolving; they are redefining the attack surface.
Security leaders must respond not incrementally, but structurally: by eliminating outdated authentication, hardening human trust pathways, and reinforcing digital infrastructure against threats that no longer wait. The threats are defined. The response must now be decisive.
Confronting the New Frontline of Enterprise Threats – AI at the Edge
AI Security: From Experimentation to Active Threat Surface
AI agents are no longer experimental—they are operationally embedded across enterprise workflows, interfacing directly with core systems, proprietary data, and user identities. As these agents scale, they are increasingly becoming high-value targets. The warning is clear and immediate: AI is not secure by default. Enterprise adoption has accelerated faster than the evolution of its corresponding security architecture, leaving significant gaps exploitable by adversaries.
These adversaries operate without the friction of procurement, regulation, or institutional inertia. They iterate in real time, weaponizing our own tools—models, APIs, and autonomous agents—against us. Meanwhile, institutional defense mechanisms remain rooted in legacy perimeter models and outdated telemetry, structurally incapable of countering threats designed natively for an AI-first ecosystem.
Compounding this risk is the troubling erosion of public cyber defense infrastructure. The proposed $500 million reduction to CISA funding exemplifies a misguided shift: treating foundational cybersecurity as discretionary even as threat velocity increases. State-aligned actors are not hesitating; they are scaling operations, innovating rapidly, and subverting systems at the identity and trust layer.
Emerging Threat Realities: Selected Incidents and Tactics
- Canadian Utility Breach: Nova Scotia Power’s corporate IT environment was targeted. While grid operations were reportedly unaffected, the incident revealed dangerous IT/OT segmentation failures, highlighting broader systemic vulnerabilities in infrastructure protection.
- Ascension Health Systems Ransomware Attack: A coordinated ransomware event disrupted hospital operations, forcing emergency service reroutes and patient care delays. The intrusion vector is under investigation but aligns with previously exploited software supply chain vulnerabilities.
- APT29 / Cozy Bear – Identity Infrastructure Targeting: Renewed campaigns utilize “Magic Web” malware to compromise ADFS authentication systems, achieving persistent privilege escalation via trust path exploitation—foreshadowing broader assaults on hybrid identity architectures.
- Chinese Threat Activity – Supply Chain and Identity Exploits: A shift toward adversary-in-the-middle attacks and hijacked update channels enables stealthy infiltration, circumventing conventional detection through misconfigurations in federation protocols and CI/CD pipelines.
AI-Specific Attack Surface: Active Exploits and Systemic Risks
- Prompt Injection – DeepSeek R1 Breach: Researchers demonstrated full bypass of guardrails via prompt injection, underscoring the failure of current context isolation models. The attack success rate was 100%, with exploit vectors published publicly, elevating urgency for AI-specific security hardening.
- Langflow Vulnerability Disclosure: Langflow’s AI workflow builder was added to CISA’s Known Exploited Vulnerabilities list shortly after proof-of-concept publication. The speed at which open-source AI tools are adopted—and exploited—exceeds the defensive response capacity of most organizations.
- Third-Party Exploits – SonicWall, Apache Pinot, SAP NetWeaver: All suffered active exploitation prior to patch application in production. These incidents reaffirm the imperative for vendors to maintain transparent, high-velocity vulnerability disclosure practices—and for enterprise teams to implement preemptive validation protocols.
A New Operational Paradigm
This is not a transitory phase. It is a directional shift in the security landscape. AI-native threats are targeting the foundations of digital trust—identity, autonomy, and federation. Organizations must evolve accordingly. Defending legacy perimeters against adversaries operating in real time with adaptive, AI-powered tooling is no longer viable. The operational imperative is clear: secure AI at the core, restructure identity systems for resilience, and restore cyber infrastructure investment before the next breach outpaces our ability to respond.
Preparing for the 2028 Humanoid Robotics Boom: A Worldwide Socioeconomic Shift
As we approach 2028, humanoid robots stand poised to redefine labor markets worldwide. Their rapid deployment threatens to outpace conventional job creation, sparking widespread employment shifts that demand urgent action. Policymakers, businesses, and communities must unite now to harness this transformative technology, or risk socio-economic fallout that could reshape the global landscape.
Google’s Hesitancy to Compare Willow on Traditional Quantum Benchmarks
Google’s decision to highlight Random Circuit Sampling is less about withholding information and more about strategically focusing on a task that demonstrates Willow’s strengths while sidestepping the shortcomings that still plague the quantum industry.
Novel Threats and Vulnerabilities to Combat in 2025 and Beyond
As digital technologies continue to penetrate every aspect of modern life, the escalation of advanced cyber threats calls for proactive defense mechanisms and a rigorous commitment to cybersecurity innovations.
The Rise of HiatusRAT: A New Threat to IoT Security
The emergence of HiatusRAT as a sophisticated, IoT-focused Remote Access Trojan (RAT) marks a critical juncture in the security landscape, heralding a new era of risk for enterprises, governmental institutions, and defense-sector organizations.
The Story of Fluoride in Water: Science, Public Health, and the Dark Possibility of Corruption
The hidden danger of excessive fluoride levels, fueled by corruption and secrecy, could quietly damage public health on a massive scale.
The Risks of Monopolistic Security Firms: A Cautionary Tale
The unchecked expansion of a single entity, now controlling both the security of millions of devices and vast amounts of sensitive data, poses unprecedented risks to both individual privacy and the stability of the broader digital ecosystem.
Protecting Your Digital Life: The Power of AI and Cloud-Based Anti-Malware Solutions
Cyber threats like malware, ransomware, phishing, and data breaches have become more advanced and widespread, targeting not just large corporations but also individual users and small businesses.
The Salt Typhoon: A Wake-Up Call for Cybersecurity in the Corporate World
An in-depth look at how the Salt Typhoon breach unfolded, the extent of its damage, and how similar attacks could potentially unfold in the future.
Securing the Cloud: A Comprehensive Guide to Understanding Risks and Defenses
In today’s digital era, cloud computing has revolutionized how businesses, governments, and individuals store and manage their data. Cloud backups, in particular, are essential for ensuring data integrity, continuity, and disaster recovery. However, as cyberattackers become more sophisticated, they are increasingly targeting cloud environments, making it imperative to understand the risks involved and how to defend against them.
This article provides a detailed exploration of the risks posed to cloud backups and the proactive measures required to mitigate them.
1. Why Cloud Backups Are Strategic Targets
Cloud backups store critical information—ranging from personal data to business records and even government secrets. While they are designed to offer security and accessibility, their strategic importance makes them a prime target for attackers. A compromised backup can disrupt operations, cause massive data breaches, and erode trust in cloud services.
Attackers can delete, alter, or encrypt backup data, undermining the reliability of cloud services. This not only halts business operations but also affects disaster recovery processes. The loss of backups leaves organizations vulnerable, with potentially catastrophic consequences.
2. Ransomware Attacks: The Silent Threat to Cloud Backups
Ransomware attacks have evolved to become one of the most significant threats to cloud environments. Modern ransomware is often designed to target both active files and cloud backups, leaving organizations with few options to recover their data.
Attackers gain access through vulnerabilities, misconfigurations, or weak authentication measures. Once inside, they can encrypt or delete backup files, forcing organizations to pay a ransom or face operational downtime. The 2020 Veeam Cloud Backup attack is a stark reminder of how such vulnerabilities can be exploited.
3. Data Manipulation: The Hidden Danger
Beyond encryption and deletion, attackers can subtly manipulate data within cloud backups. For example, altering financial records can lead to incorrect reporting or fraudulent transactions. Such manipulations often go undetected until the corrupted data is restored, causing operational and reputational damage.
For governments, tampering with classified data could lead to disinformation campaigns or diplomatic crises. The implications of compromised data integrity are far-reaching, affecting not just the targeted entity but also its stakeholders.
4. Consumers: The Overlooked Victims
While enterprises are often the primary focus, individual consumers are equally vulnerable. Cloud services like iCloud and Google Drive store sensitive personal information, including photos, contacts, and documents. A breach in these services can lead to identity theft, blackmail, or data leaks.
Phishing attacks are a common tactic used to exploit consumer cloud backups. Attackers trick users into sharing credentials, granting them access to personal data across devices. This interconnected ecosystem makes individual consumers an attractive target for cybercriminals.
5. Misconfigurations and Insider Threats
Misconfigured cloud backups can expose sensitive data to unauthorized access. For example, backups without encryption or with overly permissive access controls are easy targets for attackers.
Insider threats, whether intentional or accidental, also pose a significant risk. Employees with elevated access can leak, modify, or delete backup data. Without proper monitoring and security protocols, such threats can go undetected until it’s too late.
6. Disruption of Critical Infrastructure
Attackers targeting cloud backups can disrupt critical infrastructure, including healthcare, energy, and municipal services. The 2021 ransomware attack on Ireland’s Health Service Executive highlighted how such incidents can delay essential services.
If backup systems for critical infrastructure are compromised, recovery becomes significantly more challenging, leading to prolonged outages and cascading effects on society.
7. Trust and Transparency: The Need for Accountability
As reliance on cloud services grows, trust in providers becomes essential. Providers must ensure robust security measures, including encryption, access controls, and continuous monitoring. Transparency about vulnerabilities and security practices builds confidence among users.
The responsibility, however, is shared. Users must also follow best practices, such as securing access credentials and enabling multi-factor authentication, to protect their data.
8. Proactive Defense Strategies for Everyone
For Individuals:
- Use strong, unique passwords and enable multi-factor authentication (MFA) for cloud accounts.
- Regularly back up data to a secure, offline location.
- Stay alert to phishing attempts and avoid sharing credentials.
For Businesses:
- Invest in endpoint detection and response (EDR) solutions to monitor and mitigate threats.
- Implement zero-trust security frameworks to limit access based on user roles and behaviors.
- Train employees to recognize social engineering tactics, such as phishing and pretexting.
For Governments:
- Develop national cybersecurity policies and collaborate with international partners to address global threats.
- Invest in threat intelligence to identify and respond to emerging risks.
- Mandate stringent security standards for critical infrastructure and cloud providers.
9. Future-Proofing Cloud Security
As attackers refine their methods, the cybersecurity landscape must evolve. Technologies like artificial intelligence (AI) and machine learning (ML) are being used to predict and counter threats in real-time. Additionally, advancements in quantum encryption and decentralized cloud solutions may offer new layers of protection.
The integration of cybersecurity into cloud backup systems is no longer optional; it’s a necessity. Businesses, governments, and individuals must adopt a proactive approach to mitigate risks, ensuring that cloud environments remain a secure foundation for modern digital operations.
Conclusion: Staying Vigilant in a Dynamic Threat Landscape
Cloud computing has unlocked unparalleled possibilities for innovation and growth, but it also presents unique challenges. By understanding the risks associated with cloud backups and implementing robust defense mechanisms, we can navigate this evolving landscape with confidence.
From ransomware attacks to insider threats, the stakes are high. It’s time for everyone—individuals, businesses, and governments—to act decisively. After all, in the interconnected world of cloud computing, a single breach can ripple across the globe, affecting us all.
Let vigilance and preparation guide us toward a secure digital future.
Evolution of AI-Driven Social Engineering: Understanding the Threat and Defenses
The evolution of artificial intelligence (AI) has led to groundbreaking advances in many fields, from healthcare to transportation, and even in the realm of cybersecurity. However, the same technology that enables progress also opens the door to new vulnerabilities. Among the most insidious threats AI poses today is its ability to enhance social engineering attacks—exploiting human psychology and trust to manipulate individuals, organizations, and even governments.
Social engineering traditionally relied on human traits such as trust, urgency, and fear to deceive people into divulging sensitive information. With AI’s rise, the sophistication of these tactics has grown exponentially. AI-driven social engineering combines advanced machine learning, natural language processing, and vast data analytics to exploit cognitive biases, manipulate emotions, and create personalized attacks that are difficult to detect. This article explores the evolution of AI-driven social engineering, how it manipulates human perceptions, and how both individuals and institutions can defend against these threats.
How AI Overcomes Human Perceptions
Humans are naturally susceptible to social engineering because of our cognitive biases and emotional triggers. We tend to trust information that aligns with our existing beliefs or comes from familiar sources. AI leverages this tendency, but with the added power of automation, speed, and personalization.
- Advanced Data Analysis: AI systems can process and analyze vast amounts of data from social media, public records, and other online sources. This enables attackers to create highly personalized phishing attempts, tailored to exploit specific vulnerabilities. The attacker may know an individual’s hobbies, work relationships, and even recent emotional states, all of which can be used to craft a message that feels credible and urgent.
- Natural Language Generation (NLG): AI models like GPT (the engine behind ChatGPT) can generate highly convincing text that mimics human communication. By automating text generation, AI-driven attackers can send out massive volumes of convincing, personalized messages at scale, drastically increasing the likelihood of success.
- Deepfake Technology: AI has also enabled the rise of deepfakes—manipulated videos or audio clips that appear to be real. These can be used for impersonating executives in organizations or even heads of state. The result is highly believable content that can be leveraged for fraud, misinformation, or psychological manipulation.
- Behavioral Analysis: Machine learning algorithms can track patterns of behavior over time, creating models of individual actions, decisions, and habits. By understanding how a person behaves online, attackers can predict how they will respond to certain messages or requests, further increasing the success rate of social engineering attacks.
Exploiting Common Ignorance About Technology and AI
A significant vulnerability in AI-driven social engineering is the general public’s lack of understanding of how AI works and the threats it poses. Most people are not aware of the sophistication of modern AI technologies and their potential to manipulate human behavior.
- Lack of AI Literacy: Many individuals are unaware of the capabilities of AI, including its ability to conduct detailed analysis of their personal lives. This ignorance makes them more likely to trust AI-generated messages or interactions without question.
- False Sense of Security: People often assume that technology is infallible or that AI systems, like chatbots, are safe because they appear to be “automated” and “non-human.” This belief can lead to a lack of skepticism and increased susceptibility to attack.
- Over-reliance on Trust: A common misconception is that AI tools are inherently trustworthy. If an attacker uses AI to craft a seemingly legitimate message or impersonate a trusted figure, victims may not question the source, assuming it’s legitimate because it’s powered by advanced technology.
What’s at Stake?
The implications of AI-driven social engineering are vast, with consequences extending beyond the individual level to businesses and governments.
- Identity Theft: Personal data extracted through social engineering can be used for identity theft, leading to financial loss and reputational damage.
- Corporate Espionage: Social engineering attacks against employees can lead to the theft of intellectual property, trade secrets, or sensitive client information.
- National Security Threats: Governments can become targets of AI-driven misinformation or impersonation campaigns, leading to disruptions in political processes, election integrity, and national security.
- Public Trust: As these attacks become more sophisticated, they have the potential to erode public trust in institutions, including corporations, governments, and technology platforms.
Methodologies Used in AI-Driven Social Engineering Attacks
Social engineering, when enhanced by AI, uses several sophisticated techniques to manipulate victims:
- Phishing and Spear-Phishing: AI can personalize phishing attempts, tailoring messages to individuals’ behavior, language, and preferences. It can even adjust its tone and urgency based on real-time responses from the victim.
- Vishing (Voice Phishing): AI-powered voice synthesis can mimic a person’s voice with remarkable accuracy. Attackers can use AI to simulate phone calls from executives or bank representatives, manipulating victims into revealing personal or financial information.
- Smishing (SMS Phishing): With AI, smishing attacks can be automated and highly targeted, using data-driven insights to craft convincing messages. The use of fake URLs and convincing social engineering messages can trick individuals into downloading malware or providing sensitive information.
- Deepfake Impersonation: Deepfake technology, powered by AI, is increasingly being used to impersonate voices or images of people in positions of authority. These deepfakes can manipulate people into transferring funds, leaking confidential information, or performing actions they otherwise wouldn’t.
- Psychological Manipulation: AI can be used to deploy sophisticated emotional manipulation tactics. By analyzing a person’s online interactions, AI can identify emotional triggers—such as fear, excitement, or guilt—and exploit them to induce compliance with malicious requests.
- Cognitive Bias Weaponization: Cognitive biases, such as confirmation bias (believing information that confirms pre-existing beliefs) and scarcity bias (the fear of missing out), can be weaponized by AI. Attackers can craft messages designed to exploit these biases, making the victim more likely to comply with fraudulent requests.
- Automated Communications: AI can enable automated, large-scale social engineering campaigns through bots, which can interact with users in real-time via email, social media, and even phone calls. These bots can hold convincing conversations and gather personal data without raising suspicion.
Impact on Corporations and Governments
Corporations and governments are high-value targets for AI-driven social engineering attacks. The scale and sophistication of these attacks can have devastating consequences.
- Corporate Impact: Phishing and social engineering attacks on employees can result in data breaches, financial losses, or reputational damage. AI makes it easier for attackers to impersonate senior leaders, bypassing security measures like two-factor authentication and compromising sensitive corporate systems.
- Government Impact: AI-driven social engineering can undermine trust in government institutions by creating deepfake videos or disseminating disinformation. It can also be used in targeted attacks on public figures or officials, leading to political manipulation or public unrest.
Preparations and Defense Strategies
For Regular People
- AI Literacy and Awareness: Understanding the basics of AI can help individuals recognize when they are being targeted by sophisticated social engineering. Regular people should learn about common phishing tactics and familiarize themselves with the signs of a scam.
- Multi-Factor Authentication (MFA): Enabling MFA on personal accounts is one of the most effective defenses against social engineering. Even if an attacker gains access to personal information, MFA provides an additional layer of security.
- Skepticism and Verification: Always verify unexpected messages, especially those asking for sensitive information or urgent action. Call the person or organization directly using known contact information.
For Corporates
- Employee Training: Regular training on recognizing phishing and social engineering tactics is essential. Employees should be encouraged to question unusual requests, especially those that bypass normal protocols.
- AI-Driven Threat Detection: Corporations can deploy AI-powered security systems to detect suspicious activity, such as unusual email patterns or attempts to impersonate senior executives (CEO fraud).
- Zero-Trust Architecture: The zero-trust model assumes that no one, inside or outside the network, should be trusted by default. Corporations should implement strict identity and access controls, continuous monitoring, and authentication protocols.
- Incident Response Plan: Having a clear, tested incident response plan for social engineering attacks is critical. Employees should know how to report suspicious activity quickly, and IT teams should be prepared to respond immediately.
For Governments
- Public Education Campaigns: Governments should educate citizens about AI-driven social engineering threats, emphasizing critical thinking and skepticism in the face of unsolicited communications.
- Advanced Threat Intelligence: Governments can employ AI-based security systems to analyze large datasets for signs of social engineering attacks or misinformation campaigns.
- Legislative Oversight: Governments need to implement and enforce laws that regulate the use of AI and deepfake technologies, holding malicious actors accountable.
- Collaborative Defense: Governments should work with the private sector, international allies, and cybersecurity firms to share threat intelligence and create a united front against AI-driven social engineering.
The evolution of AI has drastically changed the landscape of social engineering. With the ability to personalize, automate, and scale attacks, AI makes it easier for malicious actors to exploit human vulnerabilities and bypass traditional security defenses. However, with awareness, education, and strategic defenses, individuals, corporations, and governments can mitigate the risks posed by AI-driven social engineering and defend against these sophisticated threats.
As AI technology continues to evolve, so too will the tactics of attackers. The key to staying ahead lies in embracing proactive defense mechanisms—such as zero-trust architectures, continuous monitoring, and user education—that can neutralize these emerging threats.
Understanding the Threat of Cyberattacks on Cloud-Hosted Businesses
As small business owners and startup companies increasingly turn to cloud hosting for their websites and operations, it’s vital to understand the potential risks involved, especially from sophisticated cybercriminal groups. Recently, Microsoft has reported on a threat actor known as Storm-0501, a financially motivated cybercriminal group that has been launching multi-faceted attacks on hybrid cloud environments across various sectors in the United States, including government, manufacturing, and law enforcement.
What is Storm-0501?
Storm-0501 has been active since 2021, originally targeting U.S. school districts with ransomware known as Sabbath. Over time, this group has evolved into a Ransomware-as-a-Service (RaaS) provider, deploying various strains of ransomware, including Hive, BlackCat, and Embargo. Their operations have become increasingly sophisticated, leveraging a mix of commodity and open-source tools to infiltrate both on-premises systems and cloud environments.
The Threat Landscape
For businesses that host their operations in the cloud, the threat posed by groups like Storm-0501 is significant. They are known for:
- Infiltration: Using a variety of methods, including exploiting vulnerabilities in widely-used software like Zoho ManageEngine and Citrix NetScaler, to gain unauthorized access to systems.
- Data Exfiltration: Once inside, they can steal sensitive data and credentials, which allows them to move laterally between on-premises and cloud environments.
- Persistent Backdoor Access: Storm-0501 often establishes long-term access to systems, making it easier for them to execute future attacks or deploy ransomware at a later stage.
- Ransomware Deployment: Their focus is on extortion, using advanced encryption techniques to lock down data and demanding payment for its release.
The Risk to Cloud-Hosted AI Tools
One critical aspect to be aware of is that AI tools deployed through cloud services can also be vulnerable to such attacks. When these tools are integrated into your operations, they become part of your overall digital environment. If a threat actor like Storm-0501 gains access, they can exploit these tools to execute their plans, making it essential for businesses using cloud-hosted AI solutions to adopt robust security measures.
Strengthening Your Defenses
Given the growing sophistication of cyber threats, here are some best practices for small business owners and startups to consider:
- Regular Software Updates: Keep all software up to date to patch vulnerabilities that could be exploited by attackers.
- Strong Authentication: Implement multi-factor authentication (MFA) to protect accounts and reduce the risk of credential theft.
- Employee Training: Educate employees about phishing and social engineering tactics, as these are common methods used by attackers to gain initial access.
- Data Backups: Regularly back up your data to minimize the impact of ransomware attacks. Ensure backups are stored securely and are not directly accessible from the network.
- Monitoring and Alerts: Use monitoring tools to detect unusual activities in your systems and set up alerts for suspicious behavior.
- Consult Cybersecurity Experts: If your resources allow, consider working with cybersecurity professionals who can help you identify vulnerabilities and strengthen your defenses.
By being aware of these threats and taking proactive steps to secure your cloud environments, you can help protect your business from potentially devastating cyberattacks. In a world where the digital landscape is constantly evolving, vigilance and preparedness are your best defenses.
Smart Financial Habits to Save and Grow Your Wealth
Discover practical strategies to save money, invest wisely, and achieve financial independence with these easy-to-understand tips.
1. Invest Before Spending
Before you start spending your money, put some of it into an investment account. This way, your savings can grow over time without you having to do much.
2. Live Below Your Means
Make sure you spend less money than you earn. The extra money you save can be invested to help build your wealth.
3. Think Long-Term
Consider every dollar you save as a chance to make more money in the future. Investing in things like Bitcoin or other assets can help your money grow over time.
4. Avoid Expensive Habits
Skip buying expensive coffee or fast food every day. Instead, make your own at home to save a lot of money over time.
5. Cancel Unnecessary Subscriptions
Regularly check your subscriptions and cancel the ones you don’t use. This can save you a significant amount of money each month.
6. DIY Projects
Doing simple home repairs and projects yourself can save you a lot on labor costs. Start with easy tasks like fixing a leak under the sink.
7. Use Public Transport Wisely
In many places, using buses or trains can be cheaper and safer than driving your own car.
8. Cut Down on Luxuries
Spend less on non-essential items like expensive clothes or gadgets. Focus on buying only what you really need.
9. Bulk Buy Essentials
Buying items like rice, flour, toilet paper, and meats in large quantities can reduce your grocery bills.
10. Energy Efficiency
Make your home more energy-efficient to save on utility bills. Consider installing solar panels if possible.
11. Resist Lifestyle Creep
As your income increases, avoid the temptation to spend more. Keep your living expenses the same to save more money.
12. Maximize Savings on Essentials
Shop at discount stores and buy in bulk from places like Costco or Sam’s Club to save on everyday items.
13. Sell Unused Items
Declutter your home and sell things you no longer need. This can give you extra income.
14. Use High-Interest Savings Accounts
Put your savings into accounts that offer higher interest rates to earn more money over time.
15. Avoid Financing for Cars
Instead of financing a new car, save up and buy a used car outright. This can save you money on interest and other fees. Also, consider the total cost of owning a car, including fuel, maintenance, and depreciation. Sometimes, leasing can be a better option.
16. Reduce Utility Usage
Be mindful of how much energy you use at home. Unplug devices when they are not in use to save on electricity bills.
17. Public Healthcare and Education
If possible, live in areas with good public healthcare and education systems to save on medical and schooling costs.
18. Limit Partying and Alcohol
Cutting back on expensive social activities can save you a lot of money.
19. Grow Your Own Food
Plant a garden to grow your own fruits and vegetables. This can reduce your grocery bills.
20. Mindful Shopping
Always compare prices and choose generic brands when possible to save money.
21. Cooking at Home
Cook meals at home and make extra portions to save time and money. Freeze the extra meals for later to avoid ordering takeout.
22. Reduce Energy Consumption
Seal any gaps in your walls, windows, and doors to keep your home warm in winter and cool in summer. This reduces the need for heating and air conditioning, saving you money.
23. Avoid Impulse Purchases
Before buying something, ask yourself if you really need it. Use a “1 in, 1 out” rule where you get rid of one item for every new item you buy.
24. Use a Shopping List
Always make a shopping list and stick to it to avoid buying unnecessary items.
25. Pay Off Credit Cards Monthly
Pay off your credit card bill every month to avoid paying interest. This helps you live within your means.
26. Pay Yourself First
Automatically transfer 10% of your paycheck into a savings account before spending on anything else. Increase the percentage as you get raises.
27. Direct Deposit to Savings
Have your paycheck directly deposited into a high-yield savings account. Only withdraw what you need for monthly bills to encourage saving.
28. Continue Saving After Paying Off Loans
Once you’ve paid off a loan or credit card, keep saving the same amount each month to build your savings.
29. Make Coffee at Home
Avoid spending money at expensive coffee shops by making your own coffee at home and taking it with you.
30. Remove Tempting Apps
Delete shopping apps like Amazon from your phone to reduce the temptation to make impulse purchases.
31. Shop at Dollar Stores
Buy everyday essentials like garbage bags, soaps, and cleaning products from dollar stores to save money. Just be careful about the quality of some items.
32. Proper Insulation
Ensure your house is well-insulated to save on heating and cooling costs. Use an infrared heat gun to find and fix any insulation problems.
33. Buy in Bulk
Purchase items like energy drinks by the case to save 30%-40% compared to buying individual cans.
34. Invest in Quality Hobbies
When you buy items for your hobbies, choose high-quality products. They often last longer and can be resold at a good price if needed.
By following these simple tips, you can save a lot of money, invest wisely, and achieve financial stability.
Combating Scams: Strategies for Individuals, Companies, CEOs, and Government Agencies
National Slam the Scam Day, observed on March 7th, serves as a reminder to take proactive measures against scams and safeguard personal, private, and government data.
Understanding Trojan.HTML.Phishing Email and Threat Prevention
Explore the insidious Trojan.HTML.Phishing threat and its prevalence via email. Discover how it spreads, the techniques cybercriminals use to deceive, and the potential consequences for those who fall into its trap. We also provide essential tips on safeguarding yourself against such attacks, ensuring you can navigate your digital communications safely and securely. Don’t miss out on this valuable information to protect your online presence.
Comprehensive Visual Guide for Installing and Running Kali Linux on Apple Silicon Mac for Free
Discover how you can install, setup, configure and tweak Kali Linux on UTM Virtual Machine platform that can run on Apple Silicon Mac offering fast and fluid Mac like performance.