Learn how you can achieve seamless Virtual Machine experience running Kali over UTM on an Apple Silicon Mac – absolutely free.
Posts/Articles
Recover, Reinstate, Prevent and Regain Control over Suspected Credit Card Transaction
Learn how to lock your credit card when facing suspicious activity, unauthorized purchases, loss, or identity theft. Be proactive, report incidents immediately, freeze your account, and dispute fraudulent charges. Stay vigilant, update passwords, and set up account alerts to safeguard your hard-earned money.
A Guide to Navigating Data Collection and Sharing During Computer Setup
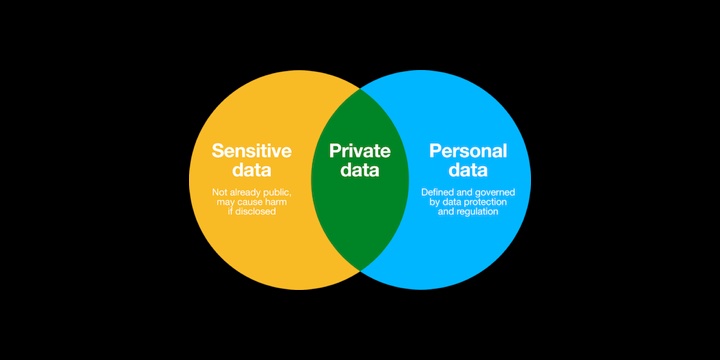
Do you realize that during your Mac or PC setup process, there are data collection and sharing consents tailored to track most of the activities you engage in across your digital realm? Learn how to make informed decisions about what data you are comfortable sharing and what you wish to keep private.
Unmasking the Scammers: Protecting Yourself from Fake Websites and Celebrity Endorsement Scams
Have you ever come across a website that seemed too good to be true, offering overwhelming benefits and endorsed by your favorite celebrity? It’s important to be aware of the tactics scammers employ to create fake sites that deceive unsuspecting individuals, luring them into their traps. By understanding their strategies, we can take precautionary measures to safeguard ourselves from falling victim to these scams.
Unveiling the Fine Prints: Are We Sacrificing Privacy for Convenience?
Are we sacrificing privacy for convenience by ignoring the fine prints of online service agreements? In our fast-paced lives, we often overlook the hidden provisions that could compromise our personal information. This article highlights the importance of understanding and exploring the implications of terms and conditions. It emphasizes the need for awareness, education, and responsible practices to protect our privacy. By demanding transparency and reclaiming control over our data, we can strive for a delicate balance that preserves our rights while embracing the benefits of the digital age.
Enhancing Credit Card Security: The Power of Virtual Credit Card Numbers
Learn how virtual credit card numbers enhance credit card security by preventing data breaches, limiting validity and usage, and offering control over spending limits. Explore the advantages of this innovative solution, safeguarding online transactions from fraud and unauthorized charges. Protect your financial information and gain peace of mind while making purchases online.
The Achilles Heel of WordPress: Exploring the Authentication Bypass Vulnerability
Uncover the potential impact of the authentication bypass vulnerability on your WordPress site’s security. Delve into the aftermath of such attacks, which include unauthorized content manipulation, data theft, and SEO manipulation. This comprehensive article provides insights into proactive measures that can effectively address this vulnerability. Explore the significance of theme and plugin security, and discover essential best practices such as sourcing from trusted developers, regular updates, removing or disabling unused components, and staying informed about reported vulnerabilities. By implementing these strategies, you can safeguard your WordPress site and reinforce its security against potential authentication bypass exploits.
Ensuring Secure Remote Support Sessions: Protecting Client Systems from Session Hijacking Attacks
Learn how to secure remote support sessions and protect client systems from session hijacking attacks. Implement best practices, educate clients, and ensure firewall, antivirus, and port security. Enhance remote session termination and post-session security for a robust and secure support environment.
Safeguarding US Government Agencies Against Persistent Threats
Discover effective strategies for US government agencies to safeguard their data, systems, and networks from cybercriminals and foreign adversaries. Learn how a multi-layered defense strategy, cybersecurity awareness training, collaboration and information sharing, risk management, advanced authentication and encryption techniques, and continuous monitoring can fortify defenses and mitigate cyber threats. Prioritize cybersecurity investments to protect critical infrastructure and sensitive information from persistent and evolving attacks.
Why Saving Credit Cards and Billing Information Online should be Avoided
Discover why it is crucial to avoid saving credit cards and billing information on websites while making online purchases. Learn about the risks of data breaches, identity theft, unauthorized transactions, and the importance of maintaining control over your financial security.
Safeguarding your Private Information on WordPress Personal Websites Amidst Growing Exploitation of Plugin and Addon Vulnerabilities
WordPress personal websites and databases are at risk of exploitation due to attackers targeting vulnerabilities in plugins and site builder addons. Safeguard your private information by staying updated with security patches, evaluating trusted plugins, limiting their use, implementing strong user authentication, backing up regularly, monitoring for suspicious activity, and engaging with security experts. Protect your WordPress website and data from potential exploitation.
Protecting Your Finances: Beware of Email Messages Targeting Bank and Crypto Exchange Accounts
As cybercriminals continually evolve their tactics, it is crucial to remain vigilant and informed about email-based scams targeting bank accounts and crypto exchange accounts. By understanding the anatomy of these scams and implementing security measures, you can protect yourself from falling victim to these fraudulent schemes.
Protecting Yourself from Text/SMS Scams: Understanding the Function and Enhancing Your Security
Text/SMS scams have become a disturbingly common occurrence in today’s digital age, and it’s crucial to be aware of their deceptive tactics. These scams prey on our trust and manipulate our emotions, often catching us off guard. To shield yourself from falling victim to text/SMS scams, it’s essential to stay informed and proactive in safeguarding your personal information. By recognizing the common techniques employed by scammers and implementing effective protective measures, you can fortify your defenses and navigate the digital world with confidence.
5 Tips to Protect Your Privacy While Signing Up for an Email or Creating an Account Online
In this digital age, it’s important to safeguard your personal information. Follow these tips to protect your privacy while signing up for an email or creating an account online. Tags: online privacy, email security, account creation, password protection, two-factor authentication.
University Professors: Beware of Spyware that might Rattle your Research
As a university professor, your personal computer contains sensitive information, research data, and other critical data. However, spyware is a malicious software that can compromise your privacy, security, and productivity. It can monitor your online activities, steal your personal information, slow down your computer, and cause other types of damage. In this article, we will explore the dangers of spyware and the importance of protecting yourself from this uninvited guest at your computer party.
Beware of Public Wi-Fi: How Hackers Exploit Networks to Steal Personal Information
Public Wi-Fi networks may seem convenient, but they also pose serious risks. Hackers are known to design and exploit public Wi-Fi networks to steal personal information from unsuspecting users. Learn how to protect yourself.
Don’t Be Fooled: How Scammers Impersonate and Obtain Personal Information
Scammers are constantly looking for new ways to obtain personal information from unsuspecting victims. One of the most common tactics scammers use is impersonation. In this article, we will discuss how scammers impersonate and obtain personal information, and what you can do to protect yourself from falling victim.
How to Safely Store Private Data on a Personal Computer
Protecting your private data on a personal computer is crucial. In this article, we discuss essential steps you can take to keep your private data safe while browsing the web, writing emails, clicking links in emails and messages, downloading random contents from the internet, and other potential areas prone to private data exposure.
The Aftermath of Identity Theft: Dealing with the Consequences and Recovery
Identity theft can be a devastating experience that can leave victims feeling vulnerable and violated. From financial loss to damage to credit scores, the aftermath of identity theft can be a long and difficult road to recovery. This article discusses the steps you can take to protect yourself, repair your credit, and seek emotional support after becoming a victim of identity theft.
8 Simple Ways to Protect Your Privacy Online in 2023 – Expert Tips
Protecting personal information is crucial in the digital age. Data breaches and cyber-attacks are increasing, but simple steps can safeguard your privacy. Explore ten expert tips in this article to keep sensitive information safe from prying eyes and unauthorized access.
How does personal privacy affect us in our everyday life? Learn to Safeguard.
Explore the impact of personal privacy on individuals, organizations, and society. Understand its significance in fostering trust, its influence on technology, businesses, and government, and the consequences of privacy erosion. Safeguard your privacy, advocate for stronger legal protections with this informative article.